What is Remote Access and How does it work?
The concept of remote access has become increasingly integral to how we work, communicate, and manage our digital resources. Remote access provides the ability to connect to and use a computer or network from a location other than the one where the device or network is physically located.
In this blog, we will explore how remote access works to transform business working capabilities.
What is Remote Access?
Remote access refers to the ability to connect to and use a computer or network from a location other than the one where the system is physically located. With the help of remote access, the user can access files and documents virtually. Listed below are the primary advantages of remote access,
Flexibility and Mobility:
Remote access enables uninterrupted connectivity, allowing users to access office networks or computing environments from diverse locations. This adds mobility and flexibility to work operations, supporting collaboration independent of geographical constraints.
Cost Efficiency:
The adoption of remote access solutions reduces capital expenditures by minimizing investments in expansive physical infrastructure, such as office spaces. Remote connectivity mitigates the need for extensive on-premises facilities, thus optimizing cost structures.
Resource Management:
Remote access technologies empower IT professionals to execute diagnostic, maintenance, and management tasks on computing systems and network infrastructures from remote locations. This removes the necessity for physical presence, streamlining resource allocation, and augmenting operational efficiency.
How Does Remote Access Work?
Now that we are aware of the meaning and advantages of remote access, let us understand how a secure connection can be established between a remote device and an office server.
Remote access relies on various technologies and protocols to facilitate seamless connections between devices or networks. Here's a breakdown of the fundamental components and methods involved:
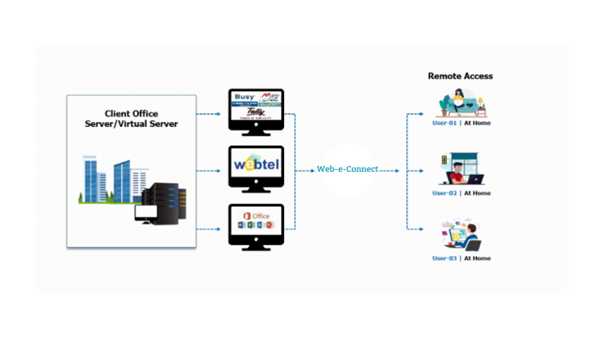
1. Network Infrastructure: Remote access typically utilizes the internet as the medium for connection. In some cases, remote access occurs within private networks, such as a corporate intranet. Virtual Private Networks (VPNs) are commonly employed to establish secure connections within these environments.
2. Protocols: Often used for accessing graphical user interfaces remotely, Remote Desktop Protocol (RDP) enables users to control a computer virtually. VPNs create encrypted tunnels over the internet, ensuring secure and private communication between devices.
3. Authentication and Security: Remote access typically requires valid user credentials (username and password) to verify the identity of the user. To enhance security, MFA adds an extra layer of protection by requiring additional verification steps, such as a code sent to a mobile device.
4. Remote Access Software: RDP solutions like Web-e-Connect enable users to access and control remote computers, often with features like file transfer and collaborative sessions.
5. Firewalls and Security Measures: Firewalls are crucial in controlling and monitoring incoming and outgoing network traffic, preventing unauthorized access. Data transmitted during remote access sessions is often encrypted to protect it from interception and unauthorized access.
What to keep in mind when choosing a Remote Access Provider?
As the digital dynamics are expanding, the market is crowding up with remote access service providers, straining the choice of the right solution. Here are some factors that must be brought into consideration when choosing a remote access tool for your business.
1. Security Concerns: Ensuring the security of remote access is an integral step to protect sensitive data. Strong authentication methods and encryption are critical besides related security methods and encryptions.
2. Uptime and Network: The quality and reliability of the network impact the user experience during remote access. Unstable connections can lead to downtime errors and inefficiencies. Web-e-Connect by Webtel provides up to 99% uptime so that your work process never stops.
3. Compliance and Regulations: Depending on the industry and geographic location, there may be specific regulations and compliance requirements related to remote access and data protection.